What did you do last Friday?
Get together with friends? Watching movies?
How about running a cyber-attack?
Have you ever noticed that vast part of high-profile cyber attacks takes place on Fridays? Apparently, this is when our defense is slightly down. This is when the danger creeps out of the corner.
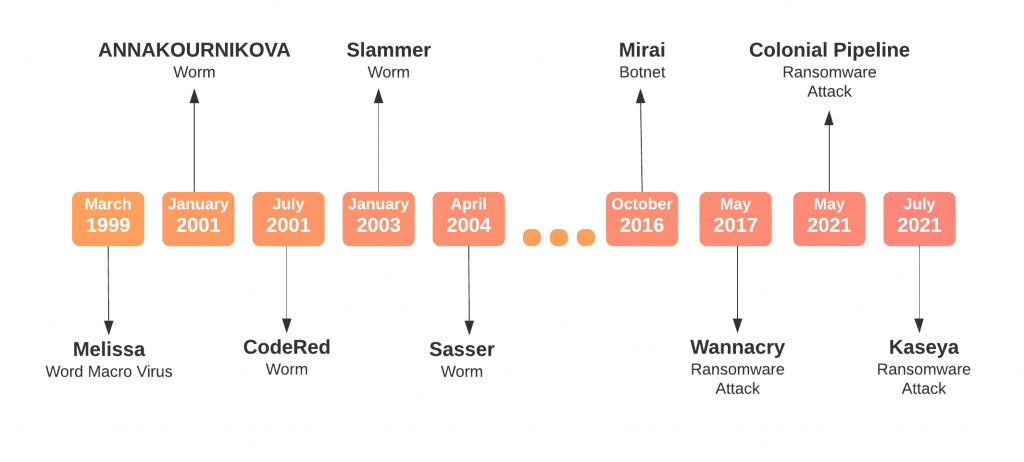
I did some digging and came up with my personal TOP 9 of Friday Cyber Attacks. This awfully biased ranking includes shut-down banks, grounded flights, strip clubs, multiple presidents, Netflix and Anna Kournikova.
Would you like to take a look?
No. 1: Wannacry
On Friday, 12th of May 2017 you could have gone to see the story of King Arthur in a rock’n’roll style from Guy Ritchie.
Or you could have witnessed the main outbreak of one of the most famous ransomware attacks in the history. Infected machines got their files encrypted and payment to restore normal use was demanded. Based on EthernalBlue exploit the malware affected 155 countries in just one day.
Hospitals, Police departments, universities, leading manufacturers, and many more across the globe were impacted. Digital society proved to be vulnerable one more time. North Koreans have never been prouder. Lazarus Group says hello!
No. 2: Sasser
It was Friday, 30th of April 2004. Gmail was exactly 30 days old. This is when Delta Air Lines had to cancel several transatlantic flights, whereas Finnish Sampo Bank came to a complete halt forced to close their 130 offices in Finland. Even the satellite communication was blocked for hours! At least this is what happened to Agence France-Presse (AFP).
Sasser was immensely successful in terms of its distribution. Using the LSASS buffer overflow vulnerability within hours spread into millions of infections causing repeated crashes and reboots of systems. BTW, have I already mentioned that Sasser was the very last participant of the Battle of Worms (see Battle of Worms in 5 Acts)?
Grounded flights and closed banks. Because of some cyber thingy. Right after turbulent 2003. There was no longer coming back. Existing status quo was finally deconstructed.
No. 3: CodeRed
That very Friday we were all still amazed by Goran Ivanisevic winning Wimbledon with a wildcard. Right? Except Microsoft. On 13th of July 2001 the giant from Redmont was just about to get some serious bashing.
Memory-resident worm – called CodeRed – was targeting Microsoft’s Internet Information Servers (IIS). They were predominantly used for web servers. The worm used – not surprisingly – a month-earlier published vulnerability called Index Server ISAPI Vulnerability. This vulnerability allowed to conduct a buffer overflow attack, which simply passes more data to a buffer than it could handle.
It was the very first successful large-scale mixed threat attack to target enterprise network. Once in the network, CodeRed was preparing Denial-of-Service (DoS) attack. There were several fixed addresses targeted. One of them was www.whitehouse.gov.
And this is why it’s my number 3. Audacity of the attack. Any intent to take down White House official website deserves a credit. You got yourself to my personal podium CodeRed!
No. 4: Colonial Pipeline
Friday 7th of May 2021. Mother’s Day weekend in the United States. People heading to meet their loved ones. Hackers heading to extort some money. To extort around $ 4.5 million to be more precise. Only several hours after the attack.
Colonial Pipeline is the one responsible for delivering gasoline, diesel, and jet fuel all the way from Texas to New York. According to Wikipedia, 45% of all fuel consumed on the East Coast arrives via this pipeline system. And it all went down. No deliveries. No gasoline. Nothing. For almost the whole week.
DarkSide group must have been proud of themselves. Or petrified. Either of two. At least this how I would feel if President of the United States promised to discuss my case:
I expect that’s one of the topics I’ll be talking about with President Putin.
President Joe Biden, 13th of May, remarks on the Colonial Pipeline incident.
No. 5: Melissa
I genuinely enjoy this story.
David Kwyjibo Smith was an enthusiast of strip clubs. Strip clubs in Florida to be exact. One of his favourite strippers was called Melissa. And this is how he named one of the first successful mass-mailing viruses. Released to the wild on Friday, 26th of March 1999.
This word macro virus was written in Microsoft’s Visual Basic and propagated itself through emails. The whole trick was to lure users to open an attachment. The subject of emails was Important Message From…. The attachment was called list.doc and contained a list of 80 pornographic websites. Once executed, the virus mailed itself to 50 addresses in users’ Address Book.
Given the times, the propagation of the virus was tremendous. It went over 100 000 infections. 300 organizations reported being severely affected, which forced them to shut down their email gateways and caused significant losses in productivity. For the very first time in the modern cyber history such a burden was put on email servers.
While world was eagerly awaiting the Millennium Bug, Mellissa took the stand. With a flair!
No. 6: Mirai
Taking down Netflix?! Well… someone has just crossed the line.
Friday, 21st of October 2016. One of the largest Distributed Denial of Service (DDoS) left Twitter, Netflix, Spotify, BBC, Amazon, GitHub, Guardian, HBO, CNN and many more inaccessible. All due to a crafty botnet code. Released to the wild. Available for everyone with basic skill and willfulness.
Mirai scanned the Internet for IoT devices that run on the ARC processor. This processor runs a stripped-down version of the Linux operating system. If the default username-and-password combo were not changed, Mirai was able to log into the device and infect it. Thousands and thousands of them got caught. And eventually got used to take down a big chunk of internet of the Eastern US.
Easily summoned botnet army to take down internet in its prime time. Sounds impressive to me.
No. 7: Slammer
At Australian Open, on Friday, 25th of January 2003, Serena Williams was winning her 5th Grand Slam title against her older sister Venus. Whereas in the dark corner of the internet emerged unknown and scary Slammer worm.
Slammer needed only 15 minutes to spread worldwide. Simple piece of code, which exploited a vulnerability known for over 6 months (!), affected 90% of all vulnerable hosts within 10 minutes. It took down 5 out of 13 world’s DNS root servers. Another 5 experienced massive packet loss.
Windows XP activation servers in Redmond were taken offline. Continental Airlines had to cancel and delay number of flights. Bank of America ATMs refused to dispense cash. In South Korea the entire internet infrastructure was knocked out.
All of that, even though, the patch for the exposed vulnerability was available at hand… Well-deserved no. 7!
No. 8: Kaseya
On 2nd of July 2021, I was heading downstair to play around with my bike. REvil gang was about to encrypt more than 1 million systems. Couple of hours later the same gang asked for a $ 70 million ransom payment. The payment was to be made by Kaseya, provider of monitoring and management tools for handling networks and endpoints.
Around 1500 medium sized companies were impacted through their managed service providers. Kaseya admitted they were the victim of a sophisticated cyberattack. Even the White House spoke! Basically, warning President Vladimir Putin to deal with problems in his own backyard. Kaseya denied paying anything whatsoever.
Notwithstanding, soon, REvil’s payment site, public domain, helpdesk chat platform and the negotiation portal were taken down. Retired? Scared? Rebranded? We shall see.
No. 9: ANNAKOURNIKOVA
Oh my. January 2001. Wikipedia goes online, George W. Bush becomes the President and Donnie Darko is still in cinemas! On Friday, 12th of January, a promise of nudity started arriving to people’s inboxes around the world. The promise of ANNAKOURNIKOVA naked blew the internet. Almost.
Off-the-shelf Visual Basic Worm Generator, simple social engineering, and several hundreds of infections within hours. Cyber users have not learned a thing from the ILOVEYOU worm. Same schema, same reaction. Although this time just for fun, the worm did not do much harm; it increased CPU utilization and clogged networks.
Jan de Wit creator of the worm even got himself a job at the municipality. No. 9 is yours Smarty-pants!
….
Friday! Finally.
Some try to relax.
Some try to catch us off-guard.
Evidence proves we regularly loose this battle.
Maciej Szulejewski
When creating this article I used threat descriptions from F-Secure Threat Description,
Virus Encyclopedia and Wikipedia. I also used Remarks by President Biden on the Colonial Pipeline Incident. Furthermore I used my own research materials.