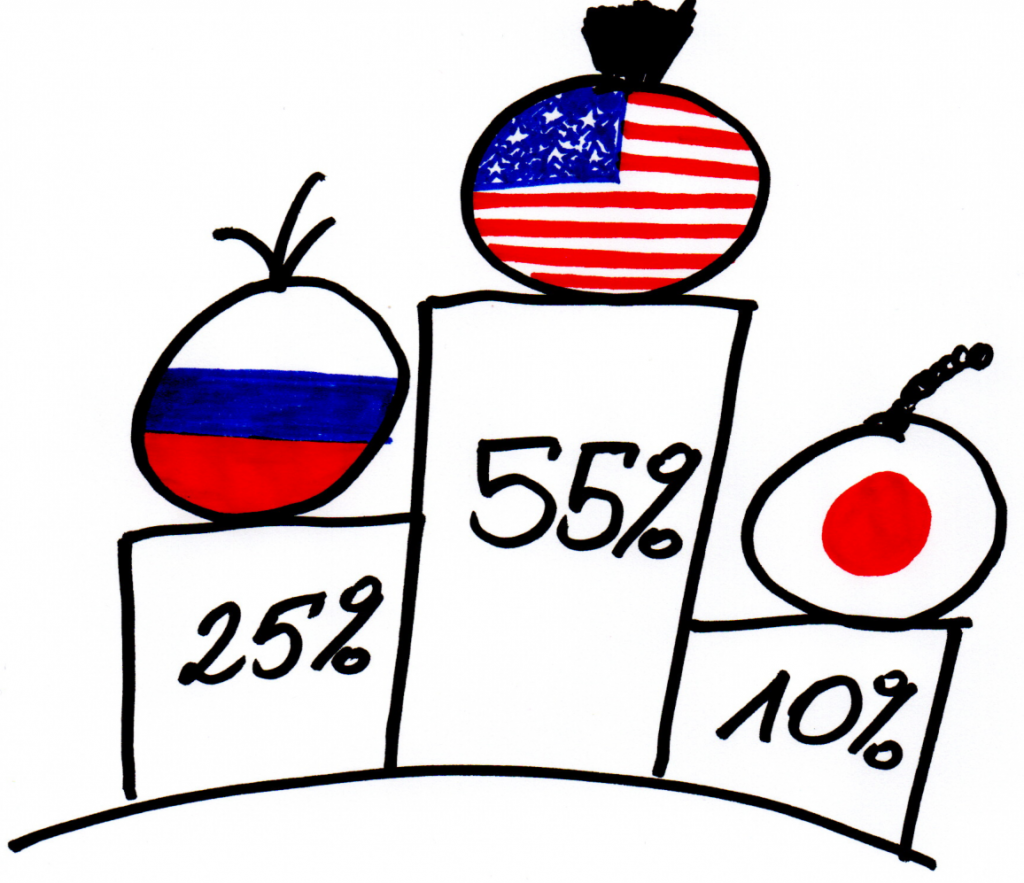
In 1999 access to the internet was a luxury. In the United States only around 35% of the population had access to worldwide network. It was just over 21% in the United Kingdom and almost exactly 20% in Germany. Russia had 1,02% of its citizens surfing through the web.
These were the golden times of jokes and funny pictures flying around in emails. The times, when although computer malware was already intrinsic to cyber reality, no one really bothered about decent anti-malware software.
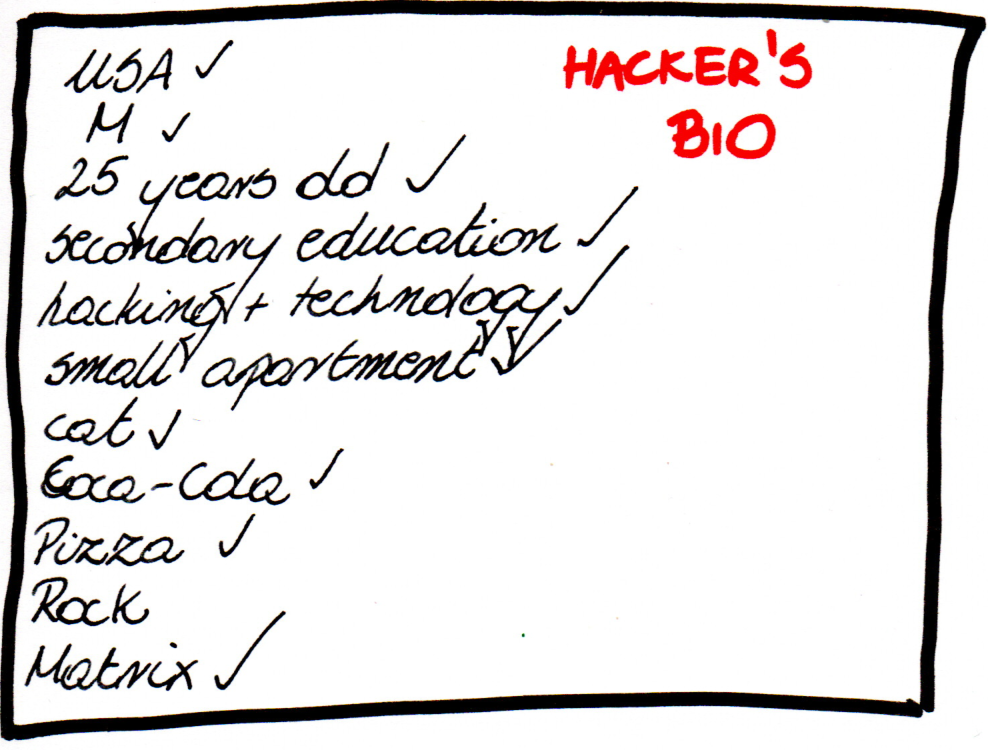
Exactly these were the times when within a 2-year span the first truly global computer malware superstars were recognized.
They reconstructed cyber reality entirely through 4 phases.
LEVEL 1 – BIRTH
One of the first successful mass-mailing viruses, the first malware rock star was born just at the brink of new millennium. At the time David Kwyjibo Smith happened to visit one of the strip clubs in Florida. One of the ladies apparently left him with an exceptional impression. As a result our story begins with the female name. The name is Melissa.
It all started on Friday, 26th of March 1999. Word macro virus was written in Microsoft’s Visual Basic and propagated itself through emails. The whole trick was to lure users to open an attachment. The subject of emails was Important Message From…. The attachment was called list.doc and contained a list of 80 pornographic websites. Once executed, the virus mailed itself to 50 addresses in users’ Address Book.
Beside mailing itself, Melissa virus went after Microsoft Word application. It infected Normal.dot template, which was used by default in all Word documents. Thus, Melissa was able to infect all new documents in order to spread itself as far as possible. Furthermore – as most malware of the time – it had a singular comedy wrinkle.
If executed when minutes of an hour matched a day of a month – e.g. 16:25 on 25th day of a month – it put the following sentence into the new document:
Twenty-two points, plus triple-word-score,
plus fifty points for using all my letters.
Game’s over. I’m outta here.
The Simpsons… and Melissa virus
Given the times, the propagation of the virus was tremendous. It went over
100 000 infections. 300 organizations reported being severely affected, which forced them to shut down their email gateways and caused significant losses in productivity. For the very first time in the modern cyber history such a burden was put on email servers (see SO MUCH FOR GOOD INTENTIONS to check the ancient era).
Luckily, all in all, Melissa did relatively little damage. However, it spread as nothing before and showed the way for others alike. The precedence was alive and kicking.
LEVEL 2 – BAPTISM
If Melissa was a rock star, then ILOVEYOU worm was the band of Beatles. Wall to wall media coverage, worldwide alerts and number of press conferences. 45 million of infections in just two days. Absolute havoc within cyber security industry. All that coming from the 24-year old student from Manilla – the capital of the Philippines – Onel De Guzman. At the beginnings of May 2000, for the very first time the world gave so much attention to a virtual incident. The first truly global computer malware was successfully baptized.
ILOVEYOU worm, written in Visual Basic script, propagated itself through email. Using Outlook or mIRC client. Due to the bug in Windows 95, the extension of the file in a mail attachment was hidden after the first dot. The worm, when executed, mailed itself to everyone in users’ Address Book. Moreover, it copied itself to the Windows System Directory and Registry, so that it could be executed whenever the system was rebooted. Unfortunately, the worm was also destroying much of victims’ hard drives by overwriting and deleting them.
Beside mass-mailing and overwriting files, ILOVEYOU payload contained
a password stealing trojan called Barok. All stolen passwords were then mailed to mailme@super.net.ph.
The idea behind the worm was straightforward. At the time the internet access in Manilla was expensive. You needed to buy a limited access directly from a service provider. Guzman decided to steal credentials from richer ones. Couple of hours after releasing ILOVEYOU into the wild, there were plenty of credentials to sift through.
Never before was there such a successful social engineering technique applied within cyber world. Simplicity is the key to brilliance, right? The subject of the email was ILOVEYOU. The attachment was LOVE-LETTER-FOR-YOU.txt.vbs. Simply perfect.
In five hours, ILOVEYOU spread across Asia, Europe and North America, some 15 times faster than the Melissa virus did when it struck a year before, infecting over 1 million computers.
Soon after starting business on May 4, the United Kingdom’s House of Commons had to take its overloaded email servers offline, as did the Ford Motor Company and even Microsoft, whose Outlook software was the primary means of spreading the virus.
James Griffiths, CNN
At the time there was no bigger story. This is what Mikko Hyppönen, CTO of F-Secure told BBC:
I remember working on the case all day from 09:41, when it started, until midnight, then going to bed only to be woken up at 3am by calls from the USA. When I hung up my phone and looked at the screen, it showed that I had received and missed 40+ phone calls during that 30-minute conference call. All those calls were coming in from partners, vendors and media. Everybody wanted to know what was happening and how to fight the outbreak.
Although a patch to fight the outbreak was available at the very same day – on 4th of May -, ILOVEYOU worm spread wide and fast. It couldn’t have been more successful. Baptism of fire was passed with the highest grade possible.
LEVEL 3 – THE RESURRECTION
So there is this young adult from the Netherlands. Computers savvy and very much interested in the art of hacking. He witnessed and paid close attention to the havoc caused by ILOVEYOU bug.
Last week I read an article about some research about the impact of the LoveLetter-virus. The title of that article says enough: Surfing people haven’t learned anything from the I Love You-virus.
Jan De Wit told wired.com
Could it be so simple to simply rerun the trap?
20-year old at the time Jan De Wit decided to follow the best practices
of hacking community. He took an off-the-shelf Visual Basic Worm Generator and went on a mission to verify if the world had learned anything from the love bug. As you may suspect, it had not.
This time the social engineering part was based on a female attractiveness.
De Wit promised his victims to show a picture of a Russian tennis player – Anna Kournikova. Once again, the generated worm propagated itself through email. Using the very same Windows vulnerability, which hid attachments extensions after the first dot. The subject was Here you have. The file was called Anna Kournikova.jpg.vbs. People were hooked like bees around the honeypot.
The biggest outbreak took place on 12th of January 2001. F-Secure estimated there were several hundreds of infections within hours. Although ANNAKOURNIKOVA worm worked alike its loving predecessor – copying itself to Windows Directory and sending itself through users’ Address Book – it did not corrupt any files on hard drives. Basically, the worm did not do much harm – it increased CPU utilization and clogged networks. However, it was again extremely virulent.
Same shit, different day. The formerly proved concept was still alive and kicking.
LEVEL 4 – THE ASCENSION
We successfully tried out Word Macro virus. We proved the promise of love and nudity will lure people into downloading whatever you wish. However, nothing that serious happened, right? Some media circus, some time-consuming cleaning up and probably guilt trips from more computer-savvy PC users. It did not cause so much trouble, though. Aspirations should be higher. Let’s get it up just one level up the ladder.
Memory-resident worm – called CodeRed later – was targeting Microsoft’s Internet Information Servers (IIS). They were predominantly used for web servers. At the time, the software was a basis for nearly 6 million websites. The worm used – not surprisingly – a month-earlier published vulnerability called Index Server ISAPI Vulnerability. This vulnerability allowed to conduct a buffer overflow attack, which simply pass more data to a buffer than it could handle. Once on the server, CodeRed scanned the network in order to find another IISs to infect them.
The worm was firstly detected on Friday, 13th of July 2001. It was the very first successful large-scale mixed threat attack to target enterprise network. Once in the network, CodeRed was preparing Denial-of-Service (DoS) attack. There were several fixed addresses targeted. One of them was www.whitehouse.gov.
The mode of operation of the worm was quite sophisticated. If a date was from 1st to 19th of a month, it was spreading as wide as possible. The actual DoS happened from 20th till 27th of the given month. Then there was an Eternal Sleep Mode, which basically was supposed to end the existence of the malware.
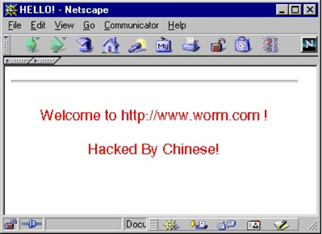
Another curiosity is a message which was defacing web pages if the language of an infected server was American English. Here we go!
Seems cut and dried, don’t you think?
The thing is that the recent malware outbreaks were still fresh and vivid. MELISSA, ILOVEYOU, ANNAKOURNIKOVA and dozens of less successful viruses experienced authorities quite heavily. The blame game started. Microsoft was an easy target, obviously.
Firstly, criticized for having their own Hotmail and Windows Update servers not entirely patched. Secondly, for seemingly unsuccessful patching campaign. Finally, for the whole notification process in general. Once the milk is spilled, what could we do? How about overcompensating with a wave of publicity?
Microsoft took a massive media announcements tour. Additionally, FBI issued an official alert, which stated that the operation of the whole internet was at risk.
Tech news site the Register and virus hoax information site Vmyths both argue that the flood of warning emails, calls to antivirus support lines and general level of hysteria can cause more damage to the internet than the worm itself.
reported by The Guardian
Number of infections reached 359 thousand on Thursday 19th and then
– exactly as programmed – started the partially successful DoS attack
(the White House site had to be moved). Along with subsequent variants
– more prolific and with installed backdoor – CodeRed was the costliest malware incident of the 2001.
After CodeRed one thing was obvious – no one and nothing is entirely secure. Endless line of potential threats. Whole new game. Whole new level.
LEVEL 5 – PREDOMINANT FEELING OF BEING VULNERABLE
At the beginning of 1999 PC users looked pretty much untroubled. Then MELISSA was born and gave a compelling lesson about the necessity of gateway filtering and scanning attachments. Actually, regular scanning in general. The outbreak of this very Word Macro virus not only brought some customers to cyber security companies, but also contributed to identification of loads of other malware already sitting comfortably on users’ machines.
Then came the actual baptism of fire. ILOVEYOU worm smashed existing status quo and proved how easily it is to hack humans. It became evident people should not be trusted. Support was needed. One of the low hanging fruits was to establish decent spam protection. Besides, PC users learned it could be useful to regularly conduct back-ups (not for long, right?). Furthermore, it was as clear as crystal the times when once-a-month signatures update was enough, were long gone.
Soon we realized we have not learned a thing. Previously known and tried concept was successfully resurrected. ANNAKOURNIKOVA worm was once again simple and terribly virulent. Basic social engineering and email attachment. Once again people! Spam protection, back-ups and regular updates could be kind of useful.
Finally, something taking security considerations into the whole new level. Although the general reaction to CodeRed might be considered as overblown, it taught no less important lesson. Enterprise networks are as vulnerable as anything else in cyber world. It explicitly showed manual patching was no longer a sufficient process. Moreover, beside health-check scanning, vulnerability scanning became a thing.
Tools and techniques used during all 4 incidents were not that sophisticated. Nor were the actual consequences for the general public. They brought, however, much greater sense. The realization this whole cyber world could be in real danger in the very near future (see: BRIEF STORY ON HOW TO FINALLY GET PEOPLE NERVOUS ABOUT THIS WHOLE CYBER SECURITY).
Maciej Szulejewski
When creating this article, I used threat descriptions from F-Secure Threat Description, Virus Encyclopedia and Wikipedia. I also used Internet access data from ourworldindata.org, A decade on from the ILOVEYOU bug from bbc.com, Anna Worm Writer Tells All from wired.com, Code Red worm from theguardian.com, I love you’: How a badly-coded computer virus caused billions in damage and exposed vulnerabilities which remain 20 years on from cnn.com.